In today's cybersecurity landscape, companies deploy an array of sophisticated tools designed to secure their software and infrastructure. Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and Cloud-Native Application Protection Platforms (CNAPP) have emerged as primary tools used to identify vulnerabilities.
However, despite the strength of these tools, many exploitable vulnerabilities still slip through the cracks.
To illustrate these gaps, we've built Broken-Flask. This simple yet insightful example clearly demonstrates how current security tools fall short and why exploitability should be your primary focus.
Plus, we’ll show how NightVision provides a more modern, context-aware approach to vulnerability scanning.
What is Broken-Flask?
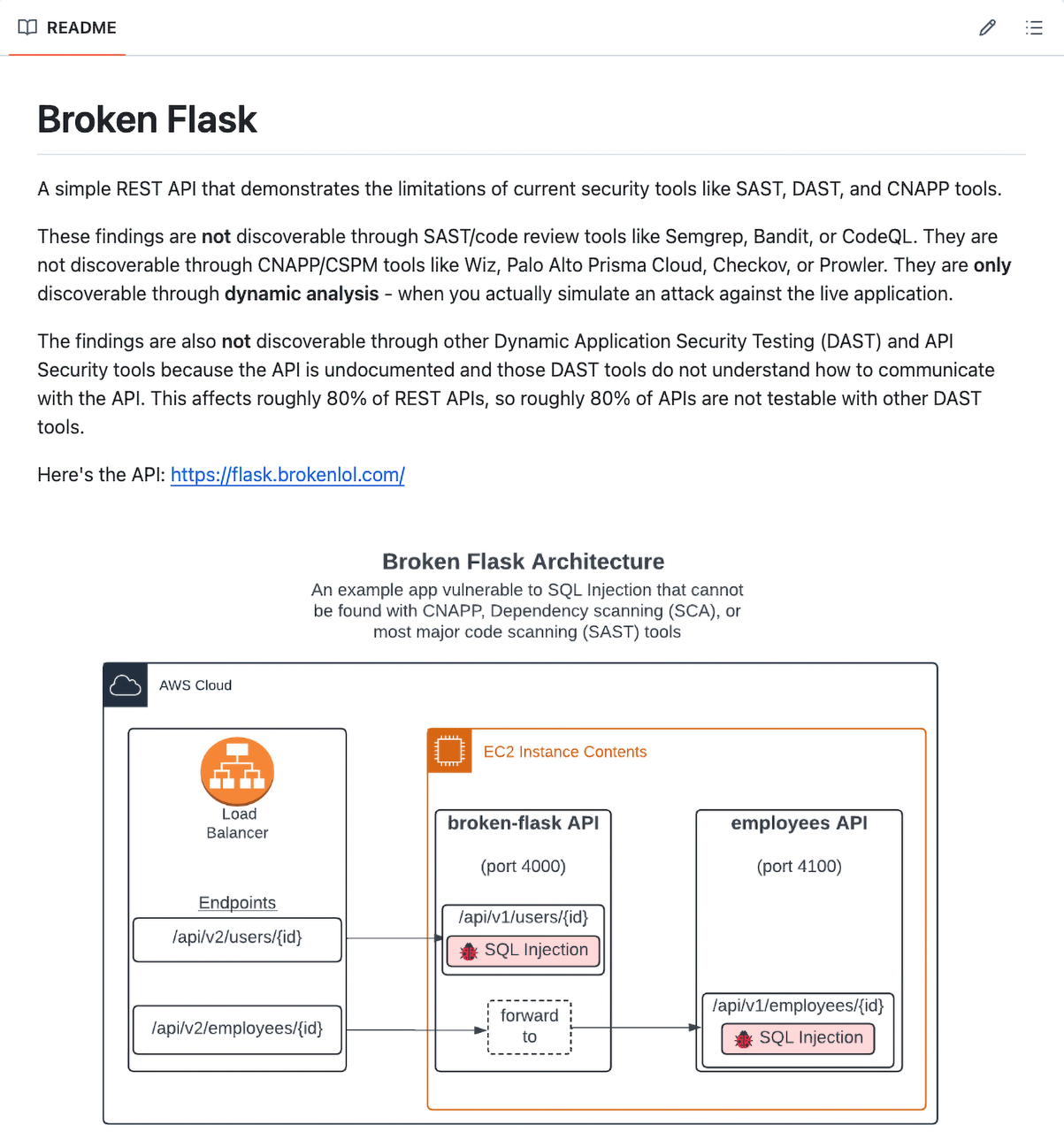
Broken-Flask is a simple, open-source, intentionally vulnerable REST API built using Python’s Flask web framework. It contains not one, but two SQL Injection vulnerabilities, both easily detectable and exploitable by attackers who are familiar with the API (and you should always assume that attackers are).
Yet these vulnerabilities go undetected by most common security tools, because they only surface during specific live interactions. Static analysis, spec-dependent scanning, and even some dynamic checks all fall short when it comes to runtime exploitability.
One SQL injection exists in a front-end API endpoint exposed directly to users, where unsanitized input is inserted into a SQL query.
The second is in a back-end API that users can’t access directly; instead, the front-end extracts a parameter from the user’s request and includes it in its own call to the back-end, where the vulnerable code is triggered.
Why SAST Tools Miss Bugs
Static Application Security Testing (SAST) tools like Semgrep, Coverity, and CodeQL analyze source code to find patterns indicative of vulnerabilities. They are valuable but have inherent limitations:
- Run-time vulnerabilities: These tools cannot detect vulnerabilities that only manifest when the application is running.
- Complex code structures: Tools like Semgrep struggle with vulnerabilities spread across multiple files.
- Business logic flaws: SAST tools do not understand nuanced application logic that could lead to vulnerabilities.
The SQL injections go undetected by SAST tools because the query is constructed dynamically over multiple steps, making it difficult for static analyzers to track the flow of untrusted input and recognize it as exploitable without runtime context.
Why SCA Can’t Protect Custom Code
Dependency analysis or Software Composition Analysis (SCA) tools, though essential for identifying vulnerabilities in third-party libraries, completely overlook custom application code vulnerabilities. While it's critical to know your dependencies, focusing solely on known CVEs leaves dangerous blind spots.
Broken-Flask's SQL Injection vulnerabilities are embedded directly in the application's custom logic, not in external dependencies, meaning SCA tools like Snyk or Dependabot will not identify these issues.
Why CNAPPs and CSPMs Miss App-Layer Flaws
Cloud-Native Application Protection Platforms (CNAPP) and Cloud Security Posture Management (CSPM) tools (Wiz, Palo Alto Prisma Cloud, Prowler) primarily focus on infrastructure misconfigurations and known vulnerabilities within cloud infrastructure components.
These tools typically create a snapshot of your cloud infrastructure, then scan the snapshot for known vulnerabilities or CVEs.
Like dependency scanners, CNAPP/CSPM tools don’t analyze custom application logic. Since the Broken‑Flask’s vulnerabilities lie within the Python code, not in its environment or third-party packages, these tools won’t detect them either.
Why DAST Tools Need More (Than) Swagger
Dynamic Application Security Testing (DAST) tools scan running applications by simulating attack scenarios. While they are well-suited for detecting vulnerabilities in live environments, most traditional DAST tools (such as OWASP ZAP) depend heavily on API documentation, like Swagger, to discover endpoints and communication patterns.
This matters because approximately 80% of REST APIs are undocumented, severely limiting traditional DAST effectiveness. Without clear documentation, tools like ZAP are blind to not only the API’s existence, but how to create valid requests, and therefore cannot scan or identify vulnerabilities within them.
In our Broken-Flask app, the API is intentionally undocumented. Consequently, DAST tools will fail to discover the critical SQL Injection vulnerabilities embedded within the APIs.
Exploitability is the Key
While security teams focus heavily on known vulnerabilities and CVEs, many overlook the most critical aspect: exploitability. A known vulnerability in a third-party package that isn't exploitable poses minimal risk, while an unknown, highly exploitable vulnerability within custom code can expose your entire organization.
Broken-Flask’s SQL Injection vulnerabilities demonstrate this critical difference. This common vulnerability, ranked #3 (A03:2021-Injection) in the OWASP Top 10, remains one of the most exploited vulnerabilities globally.
NightVision: Seeing What Others Can’t
Traditional tools like SAST, DAST, and CNAPP each tackle important parts of the AppSec puzzle, but they often generate false positives, require heavy setup, and miss exploitable vulnerabilities, especially in undocumented APIs.
NightVision is designed to overcome these weaknesses through a modern gray‑box approach that blends smart code analysis, comprehensive API discovery, and rapid DAST, all tailored for seamless developer and security integration.
NightVision's Static Analysis engine automatically discovers and documents both public and shadow APIs, even when no OpenAPI or Swagger spec exists. It builds a complete API map across your application: public endpoints, private microservices, and hidden routes, so nothing goes untested.
As these APIs are discovered, NightVision records precise file paths and line numbers, showing exactly where each route is defined in your codebase. When a vulnerability is identified through dynamic testing, NightVision ties the finding directly to its source, surfacing it in GitHub Security Alerts or other integrations, so developers can quickly trace, understand, and remediate the issue without leaving their workflow.
How NightVision Shines on Broken‑Flask
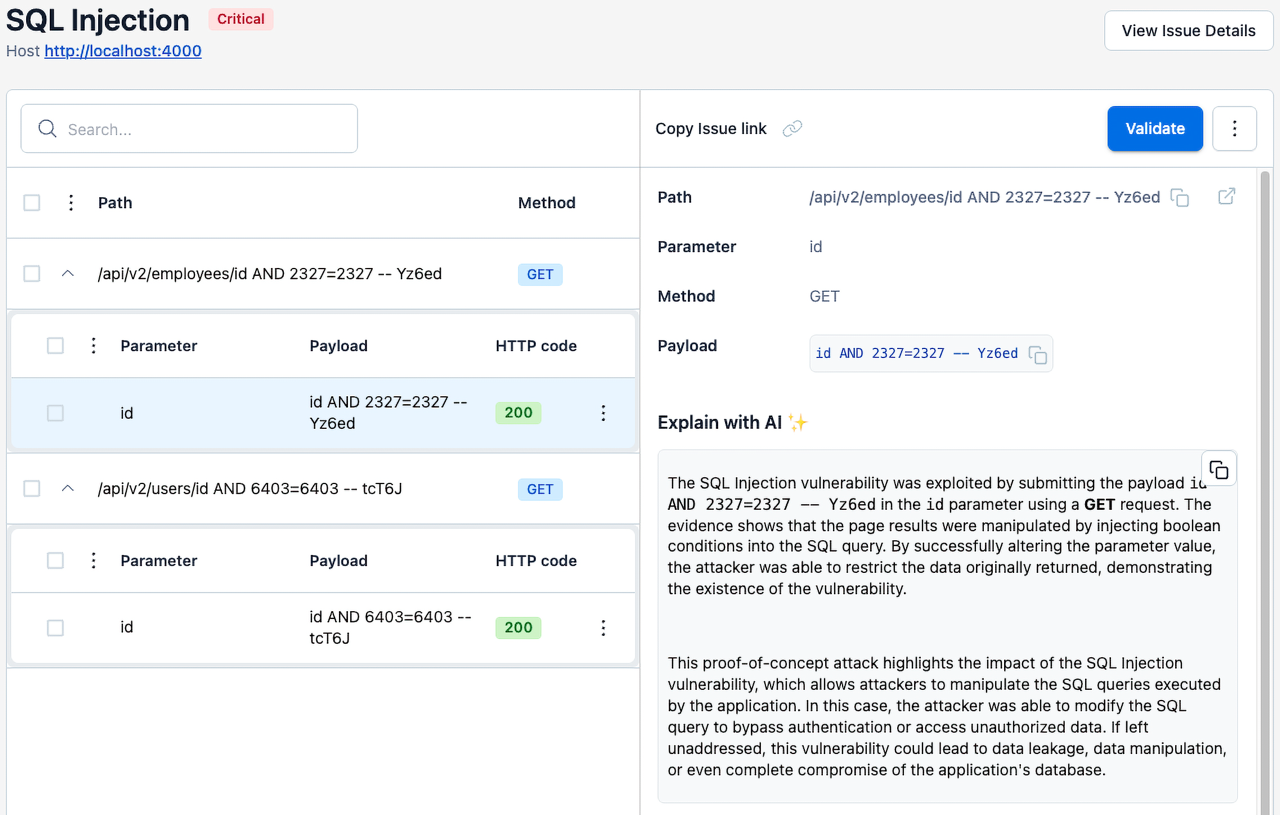
Against the Broken‑Flask API, NightVision:
- Discovers both the front‑end and back‑end endpoints by scanning the code, creating its own API documentation to use.
- Launches targeted SQL‑injection probes against each endpoint.
- Detects runtime exploitation, differentiating actual vulnerabilities from theoretical patterns.
- Maps the findings back to the vulnerable query building string in app.py, giving full context for remediation.
By marrying automated API mapping, runtime testing, and precise traceability, NightVision uncovers exactly what attackers can exploit, without manual schema setup, request scripting, or false-positive noise.
NightVision isn't just another scanner, it’s a modern, developer-first AppSec companion, built for the speed and complexity of today’s development environments. It ensures you're protected against what matters: exploitable vulnerabilities.
Conclusion
Broken-Flask clearly demonstrates that even sophisticated security tooling has inherent blind spots. Relying solely on SAST, SCA, CNAPP, or traditional DAST can leave significant vulnerabilities undiscovered, especially in custom and undocumented APIs. Understanding and actively testing for exploitability is essential for true application security.
Explore Broken-Flask here and see firsthand the limitations of conventional tooling, and how NightVision uniquely addresses these challenges.
Schedule a NightVision Demo


.svg)





.svg)